In the ever-evolving world of digital currencies, hash crypto stands as a fundamental pillar. This article aims to demystify the concept of hash cryptography, its role in the crypto world, and why it’s so crucial for blockchain technology.
Table of Contents
What is Cryptography?
Cryptography is a method of protecting information by transforming it into an unreadable format. It’s a science of secure communication, designed to allow the sender and intended recipient of a message to view its contents while preventing anyone else from doing so. The term “cryptography” comes from the Greek words “kryptos” and “graphein”, which mean “hidden” and “writing”, respectively.
Cryptography is not a new concept. It has been used for thousands of years, dating back to the ancient Egyptians and Romans. They used simple encryption methods, like shifting letters of the alphabet, to protect their messages.
In today’s digital age, cryptography has become a cornerstone of the modern information security used in many applications to protect information in computer systems and networks.
Understanding Hash Functions
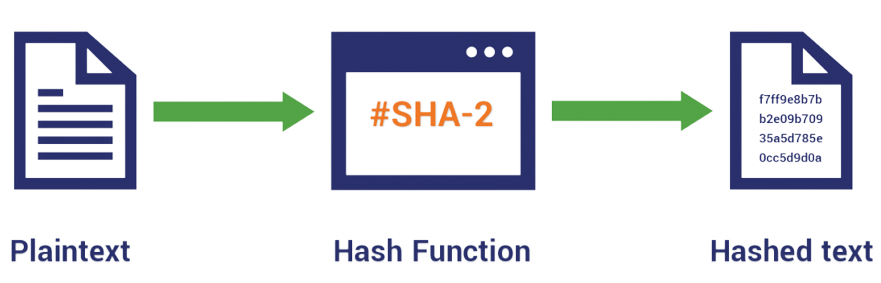
Hash functions are mathematical algorithms that take an input (or ‘message’) and return a fixed-size string of bytes, typically a hash value. The output is unique to each unique input, meaning even a minor change in input will produce a significantly different output. This property is known as the ‘avalanche effect’.
There are various types of hash functions, each with its unique characteristics and uses. Here’s a more detailed look at some of these types:
| Hash Function Type | Description | Common Use Cases | Examples |
|---|---|---|---|
| Cryptographic Hash Function | Designed to be secure against attacks. They are deterministic, meaning the same input will always produce the same output, and they produce a fixed-size output regardless of the size of the input. | Used in cryptography for data integrity, password storage, and digital signatures. | SHA-256 (used in Bitcoin), SHA-3, Blake2 |
| Checksum | A simple form of hash function used to detect errors in data. They calculate a value based on the data and send this value along with the data. The recipient can then recalculate the checksum and compare it to the received checksum to check for errors. | Used to detect errors in data transmission or storage. | CRC32, Adler-32 |
| Non-Cryptographic Hash Function | These hash functions prioritize speed and efficiency over security. They are used in applications where data needs to be quickly retrieved, rather than securely stored. | Used in data retrieval applications, such as database indexing and caching. | MurmurHash, CityHash |
Hash functions are a fundamental part of many digital systems, providing a way to process, store, and retrieve data efficiently and securely. Understanding how they work and how they are used is key to understanding many aspects of digital technology, from data storage and transmission to digital security and cryptocurrencies.
Exploring Hash Functions
Hash functions can be quite complex, especially when it comes to cryptographic hash functions used in technologies like blockchain. However, to give you a basic understanding, let’s look at a very simple hash function.
Consider a hash function that operates on strings of text. This function could work by assigning a numerical value to each letter (for example, ‘a’ = 1, ‘b’ = 2, ‘c’ = 3, and so on), and then adding up these values to create a hash.
For example, using this hash function, the word “hash” would be calculated as follows:
scssCopy codeh (8) + a (1) + s (19) + h (8) = 36
So, the hash of “hash” would be 36.
This is a very simple example and real-world hash functions are much more complex. They use advanced mathematical operations to ensure that each input produces a unique output that cannot be reversed to reveal the original input.
For instance, the SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function that produces a 256-bit (32-byte) hash value. It’s widely used in cryptographic applications and protocols, including Bitcoin. The SHA-256 algorithm operates in rounds, each of which involve several mathematical operations, including logical functions, bitwise operations, and modular arithmetic.
While the exact operations used in SHA-256 are beyond the scope of this explanation, the key point is that it’s designed to be a one-way function: it’s computationally infeasible to generate the original input given only the hash output. This is what makes it suitable for cryptographic applications.
Role of Hash Functions in Cryptography
Hash functions serve as the workhorses that underpin many of the protocols and processes that ensure the security and integrity of data. They are integral to a variety of applications, from digital signatures to data integrity checks. Here’s a closer look at how hash functions play a pivotal role in cryptography:
Data Integrity:
One of the primary uses of hash functions in cryptography is to ensure data integrity. When data is sent from one place to another, there’s always a risk that it might get corrupted or altered, whether due to malicious intent or a simple transmission error.
To mitigate this risk, the sender can create a hash of the data before sending it. The recipient can then create a hash of the received data and compare it to the original hash. If the two hashes match, the recipient can be confident that the data has not been altered in transit. If they don’t match, it’s a clear sign that the data’s integrity has been compromised.
Password Storage:
Hash functions are also commonly used in password storage. Storing passwords in plaintext is a significant security risk. If a database with plaintext passwords is breached, all user accounts are immediately compromised.
To avoid this, systems often store a hash of the password instead of the password itself. When a user enters their password, the system hashes the input and compares it to the stored hash. This way, even if the database is breached, the attacker only has access to the hashes and not the actual passwords.
Digital Signatures:
Hash functions are a key component of digital signatures, a crucial tool for verifying the authenticity of digital documents. When a digital signature is created, the document is hashed, and the hash is then encrypted with the sender’s private key. The recipient can then decrypt the hash with the sender’s public key and compare it to the hash of the received document. If the hashes match, the document is verified as authentic and untampered.
Hash functions are a fundamental part of modern cryptography. They provide a powerful tool for ensuring data integrity, securing password information, verifying digital signatures, and more. As we continue to move towards a more digital and interconnected world, the role of hash functions in cryptography is set to become even more critical.
Hash Cryptography in Blockchain
Hash cryptography is a fundamental component of blockchain technology, underpinning its core features of transparency, security, and immutability. Here’s a detailed look at how hash cryptography is used in blockchain:
Transaction Verification:
In a blockchain, each transaction is hashed and the hash value is stored in the corresponding block. This hash serves as a unique identifier for the transaction. When a user wants to verify a transaction, they can hash the transaction data and compare the result with the stored hash. If the hashes match, the transaction is verified as authentic and unaltered.
Block Linking:
Each block in a blockchain contains a hash of all the transactions within the block, as well as the hash of the previous block in the chain. This creates a chain of blocks, where each block is linked to the previous one through its hash. This structure ensures that once a block is added to the blockchain, it cannot be altered without changing the hash of every subsequent block, which provides a high level of security and immutability.
Mining and Proof of Work:

In blockchain networks like Bitcoin, hash functions are used in the mining process, which involves validating new transactions and adding them to the blockchain. Miners must solve a complex mathematical problem, which involves generating hashes until they find one that meets certain criteria. This process, known as proof of work, requires significant computational resources, making it difficult for any one entity to control the blockchain.
Creating Digital Signatures:
Hash functions are also used to create digital signatures in blockchain transactions. When a user wants to send a transaction, they first create a hash of the transaction data. This hash is then encrypted with the user’s private key to create a digital signature. The signature and the transaction data are then sent to the network. Recipients can verify the signature by decrypting it with the user’s public key and comparing the result to the hash of the received transaction data.
Popular Mining Hash Algorithms
Cryptocurrency mining involves solving complex mathematical problems using hash functions. Different cryptocurrencies use different hash algorithms for this process. Here are some of the most popular mining hash algorithms:
SHA-256:
SHA-256 (Secure Hash Algorithm 256-bit) is perhaps the most well-known hash algorithm, primarily because it’s used by Bitcoin, the first and most famous cryptocurrency. It produces a 256-bit hash and is known for its security and reliability. Mining cryptocurrencies that use SHA-256 requires a significant amount of computational power, which has led to the rise of specialized mining hardware known as ASICs (Application-Specific Integrated Circuits).
Scrypt:
Scrypt is the hash algorithm used by Litecoin, among other cryptocurrencies. It was designed to be more accessible to miners with less powerful hardware. Unlike SHA-256, which is processor-intensive, Scrypt is memory-intensive. This makes it less suitable for ASICs and more suitable for regular computers with high-end graphics cards. However, ASICs designed for Scrypt have been developed over time.
Ethash:
Ethash is the hash algorithm used by Ethereum. Initially, it was designed to resist the use of ASICs, making Ethereum mining accessible to users with regular computers. Ethash is memory-intensive, requiring a lot of RAM for efficient mining. However, over time, ASICs capable of mining Ethash have been developed, leading to a debate about ASIC vs GPU mining and the impact on Ethereum’s decentralization.
CryptoNight:
CryptoNight is the hash algorithm used by Monero and other privacy-focused cryptocurrencies. It’s designed to be suitable for mining on regular computers with CPUs and GPUs. CryptoNight is both memory-intensive and processor-intensive, making it resistant to ASICs. This aligns with Monero’s goal of ensuring that mining is decentralized and accessible to as many people as possible.
Equihash:
Equihash is used by Zcash and other cryptocurrencies. Like Ethash, Equihash was initially designed to resist ASICs, making it suitable for mining on regular computers. It’s a memory-intensive algorithm, requiring a lot of RAM for efficient mining. However, ASICs capable of mining Equihash have since been developed, sparking discussions about ASIC mining and its implications for Zcash’s decentralization.
Octopus:
Octopus is a relatively new hash algorithm used by the Conflux Network. It’s designed to be ASIC-resistant, making it more accessible to individual miners using GPUs. Octopus is memory-intensive, requiring a significant amount of RAM for efficient mining. This design choice helps to level the playing field between ASIC and GPU mining, promoting decentralization and wider participation in the Conflux Network.
RandomX:
RandomX is the hash algorithm used by Monero, replacing the previous CryptoNight algorithm. RandomX is designed to be suitable for general-purpose CPUs. It uses random code execution and memory-hard techniques to prevent ASICs from dominating the network. This aligns with Monero’s goal of ensuring that mining is decentralized and accessible to as many people as possible. The introduction of RandomX has sparked discussions about the future of ASIC and GPU mining, as it shifts the focus towards CPU mining.
Different cryptocurrencies use different hash algorithms for mining, each with its own advantages and characteristics. While some were designed to resist ASICs and promote decentralization, the development of ASICs capable of mining these algorithms has led to ongoing debates about the future of cryptocurrency mining. As the world of cryptocurrencies continues to evolve, we can expect to see new and innovative hash algorithms in the future.
Advantages and Disadvantages of Hash Cryptography
Hash cryptography, like any technology, comes with its own set of advantages and disadvantages. Understanding these can help us appreciate its role in digital security and also identify areas for potential improvement.
Advantages of Hash Cryptography:
- Data Integrity: Hash functions provide a way to ensure data integrity. Since the hash value changes with even a minor modification to the input data, it’s easy to detect if data has been tampered with. This is crucial in many applications, including data transmission and storage.
- Authentication: Hash functions are used in creating digital signatures, which are essential for authenticating the source of data or a message. This helps ensure that the data has not been altered and verifies the identity of the sender.
- Speed and Efficiency: Hash functions are computationally efficient. They can process large amounts of data quickly, making them suitable for real-time or near-real-time applications.
- Fixed Output Size: Regardless of the size of the input data, a hash function will always produce an output of a fixed size. This can be beneficial for managing and storing data.
Disadvantages of Hash Cryptography:
- Vulnerability to Attacks: While hash functions are designed to be secure, they are not impervious to attacks. For instance, a ‘collision’ occurs when two different inputs produce the same hash output. While these are rare and hash functions are designed to minimize the possibility, it is not zero.
- Irreversible: Once data has been hashed, it cannot be reversed or decrypted to retrieve the original data. While this is an advantage in terms of security, it can also be a disadvantage if the original data needs to be retrieved.
- Dependence on Algorithm Strength: The security and effectiveness of hash cryptography depend heavily on the strength of the hash algorithm used. If the algorithm has weaknesses, the hashed data may be vulnerable to attacks.
- Need for Additional Security Measures: While hash functions provide a level of security, they are often not sufficient on their own. Additional security measures, such as salt (random data added to the input of a hash function to protect against attacks), are often required.
In conclusion, hash cryptography plays a vital role in digital security, providing data integrity, authentication, and efficiency. However, it also has its limitations and vulnerabilities, which need to be considered and addressed to ensure the security of the data. As technology evolves, so too will hash cryptography, with ongoing research and development aimed at maximizing its advantages and mitigating its disadvantages.
Future of Hash Cryptography
As we continue to move towards a more digital and interconnected world, the role of hash cryptography is set to become even more critical. Here are some trends and predictions for the future of hash cryptography:
Increased Use in Blockchain and Cryptocurrencies:
The use of hash functions in blockchain technology and cryptocurrencies is likely to increase as these technologies continue to evolve and gain mainstream acceptance. Hash functions are integral to the operation of blockchains, providing data integrity, security, and transparency. As more industries start to adopt blockchain technology, we can expect to see new and innovative uses for hash cryptography.
Quantum Computing:
The advent of quantum computing presents both opportunities and challenges for hash cryptography. On the one hand, quantum computers could potentially break many current hash functions, posing a significant threat to digital security. On the other hand, they could also lead to the development of new, more secure hash functions. This is an area of active research, and the impact of quantum computing on hash cryptography will be a key issue to watch in the coming years.
Development of New Hash Functions:
As technology evolves and new threats to digital security emerge, we can expect to see the development of new hash functions. These will likely be designed to address the limitations of current hash functions and to provide greater security. For instance, there is ongoing research into hash functions that are resistant to quantum computing attacks.
Increased Regulation:
As hash cryptography becomes more widely used, it’s likely to attract increased attention from regulators. This could lead to new regulations and standards for hash functions, particularly in sensitive areas such as data protection and financial transactions. While this could pose challenges for some businesses, it could also lead to greater trust and confidence in digital transactions.
The future of hash cryptography looks set to be dynamic and exciting, with new developments in technology providing both opportunities and challenges. As we continue to rely more on digital technologies, the importance of hash cryptography in ensuring the security and integrity of our data is only set to increase.
Conclusion
Hash cryptography, a cornerstone of digital security, plays a pivotal role in our increasingly digital world. From ensuring data integrity and authenticating digital signatures to underpinning the operation of blockchain technology and cryptocurrencies, hash functions are integral to many aspects of digital communication and transactions.
We’ve delved into the intricacies of hash functions, their role in cryptography, and their application in blockchain technology. We’ve also explored popular mining hash algorithms like SHA-256, Scrypt, Ethash, CryptoNight, Equihash, Octopus, and RandomX, each with its unique characteristics and applications.
While hash cryptography offers numerous advantages such as data integrity, authentication, and computational efficiency, it’s not without its challenges. Vulnerabilities to attacks, the irreversible nature of hashing, dependence on algorithm strength, and the need for additional security measures are all aspects that need continuous research and improvement.
The future of hash cryptography is intrinsically tied to the evolution of technology. The rise of blockchain technology, the advent of quantum computing, the development of new hash functions, and increased regulation are all factors that will shape its trajectory.
As we navigate through the digital age, the importance of understanding and improving hash cryptography cannot be overstated. It’s a fascinating field that combines mathematics, computer science, and cryptography, and its role in securing our digital world is set to grow even more significant. As we continue to innovate and face new digital security challenges, hash cryptography will undoubtedly be at the forefront of many solutions.
What is hash crypto?
Hash crypto refers to the use of hash functions in cryptography. A hash function is a mathematical algorithm that takes an input and returns a fixed-size string of bytes, typically in the form of a hash value. This hash value is unique to each unique input, meaning even a minor change in input will produce a significantly different output. In the context of cryptography, hash functions are used for various purposes, including ensuring data integrity, storing passwords securely, and creating digital signatures.
How does hash cryptography work in blockchain technology?
Hash cryptography is integral to the functioning of blockchain technology. It’s used to create a unique identifier, or ‘hash’, for each block of transactions in the blockchain. This hash is then used to link blocks together in a chain, ensuring that the data within them cannot be tampered with without changing the hash and breaking the chain. Hash functions are also used in the process of mining new blocks and in creating digital signatures for transactions.
What are the advantages and disadvantages of hash cryptography?
The advantages of hash cryptography include ensuring data integrity, providing a means of authentication, and being computationally efficient. However, it also has its disadvantages. These include vulnerability to attacks (such as hash collisions), the irreversible nature of hashing (meaning once data has been hashed, it cannot be ‘unhashed’ to retrieve the original data), and the fact that the security of hash cryptography is heavily dependent on the strength of the hash algorithm used.
What is the future of hash cryptography in the crypto world?
The future of hash cryptography in the crypto world is likely to be shaped by several factors. These include the continued evolution and adoption of blockchain technology, the advent of quantum computing, the development of new hash functions, and increased regulation. As blockchain technology continues to find new applications and as new threats to digital security emerge, we can expect to see ongoing innovation and development in hash cryptography.