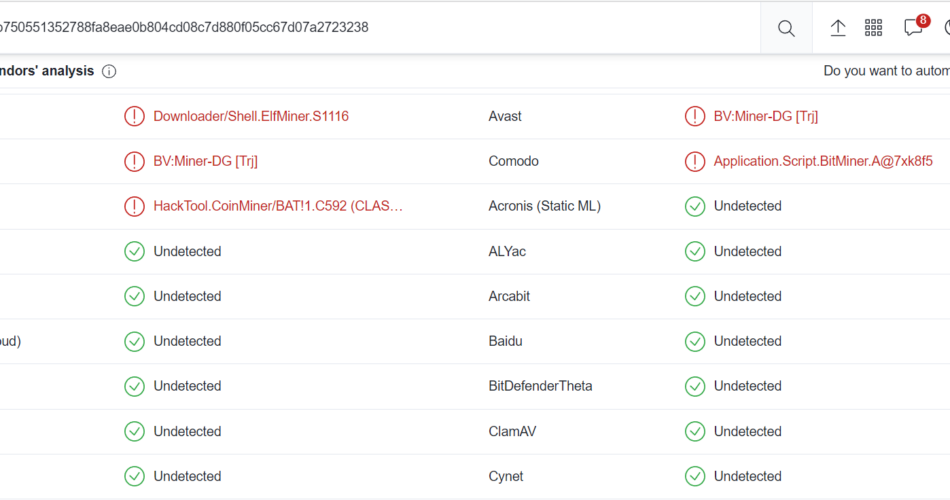
In the digital gold rush of the 21st century, cryptocurrency mining has become the new frontier. But with every frontier comes its challenges. One alarming trend that has emerged is the frequency with which crypto mining software flagged as malware. Why is this happening, and what does it mean for the average user? Let’s delve into the intricate world of crypto mining and uncover the shocking truths behind this phenomenon.
Table of Contents
What is Crypto Mining?
Crypto Mining Defined
Cryptocurrency mining, at its core, is the process by which new digital coins are introduced into circulation. It involves solving complex mathematical problems using computer hardware, which in turn validates and records transactions on a blockchain.
The Role of Mining Software
To mine effectively, one requires specialized software. This software connects the miner to the blockchain and harnesses the power of the computer’s hardware to solve the necessary problems.
Why Some Mining Software is Flagged as Malware?
Cryptocurrency mining, once a niche hobby for tech enthusiasts, has now become a mainstream activity. With the rise in popularity of cryptocurrencies, there has been a parallel increase in the number of software applications developed to facilitate the mining process. However, a perplexing trend has emerged: many of these mining software applications are being flagged as malware by antivirus programs. Let’s delve deeper into the reasons behind this phenomenon.
1. False Positives: The Unintended Consequence
The aggressive nature of modern antivirus heuristics can sometimes lead to genuine mining software being mistakenly flagged as malware. Here’s why:
- Similar Behavioral Patterns: Genuine mining software, like its malicious counterparts, uses a significant amount of computational resources. To an antivirus program, this behavior might appear suspicious, leading to a false positive.
- Heuristic Analysis: Modern antivirus solutions don’t just rely on signature-based detection; they also analyze the behavior of software. If a piece of software behaves similarly to known malware, it might be flagged, even if it’s benign.
- Overzealous Protection: With the rise in cryptojacking and other mining-related threats, some antivirus programs have adopted a more aggressive stance, flagging all mining-related activities as potentially harmful.
2. Unauthorized Resource Use
Cryptocurrency mining is a resource-intensive process. It requires a significant amount of computational power to solve the complex mathematical problems that underpin the creation of new cryptocurrency tokens. Some malicious actors have developed software that, once installed on a victim’s computer, covertly uses the computer’s resources to mine cryptocurrency. This type of software operates without the user’s knowledge or consent, effectively “stealing” their computational power. As a result, antivirus programs have been trained to detect and flag such unauthorized mining activities.
3. Cryptojacking: The Silent Threat
Cryptojacking is a more insidious form of unauthorized resource use. In this scenario, malicious actors embed scripts on websites that automatically use the website visitor’s computer resources to mine cryptocurrency. The user might notice their computer slowing down or their battery draining faster than usual, but they often remain unaware that their resources are being used for mining. Given the stealthy nature of cryptojacking, it’s no surprise that antivirus solutions actively seek out and flag such scripts.
4. Bundling with Other Malware
One of the most insidious threats is the bundling of genuine mining software with other malicious programs. This tactic, often overlooked, poses significant risks not only to individual users but also to organizations and the broader digital ecosystem. At its core, the strategy of bundling relies on deception. Malicious actors often take advantage of the reputation of legitimate mining software. By attaching their malware to these trusted programs, they can bypass the initial skepticism of potential victims. Users, believing they are downloading a genuine and safe application, inadvertently introduce harmful malware into their systems.
The Array of Bundled Threats
The types of malware bundled with mining software can vary, but they all pose significant threats:
- Keyloggers: These stealthy programs record every keystroke, capturing passwords, credit card numbers, and other sensitive information. This data can then be sent to cybercriminals, leading to identity theft, financial fraud, and more.
- Ransomware: Once activated, ransomware encrypts a user’s files, rendering them inaccessible. Victims are then extorted for money, usually in cryptocurrency, in exchange for the decryption key.
- Trojans: These malicious programs disguise themselves as legitimate software but, once installed, can give cybercriminals remote access to a victim’s computer, allowing them to steal data, install more malware, or even use the machine as part of a botnet.
- Spyware: This malware secretly monitors and collects information from the user’s device, often leading to privacy breaches.
The Risks of Malicious Mining Software
Cryptocurrency, with its promise of decentralization and financial freedom, has attracted millions worldwide. However, as with any revolutionary technology, it has also opened the door to a myriad of threats. Among these threats, malicious mining software stands out, not just for its prevalence but for the multi-faceted risks it poses. Let’s delve into the dangers that lurk behind these deceptive programs.
1. Risk of Losing Funds from Crypto Wallets
Arguably the most alarming risk associated with malicious mining software is the potential loss of funds from crypto wallets. Here’s how it happens:
- Direct Theft: Some malicious mining programs come bundled with trojans or keyloggers. Once installed, these can capture sensitive information, including the private keys to crypto wallets. With the private key in their possession, cybercriminals can easily transfer funds to their own wallets, leaving the victim with an empty balance.
- Phishing Attacks: Malicious software can redirect users to fake versions of popular crypto exchanges or wallet sites. Unsuspecting users might then enter their login credentials, giving attackers the access they need to steal funds.
2. Unauthorized Resource Use
Mining cryptocurrencies requires significant computational power. Malicious mining software, operating covertly, can harness a victim’s computer resources without their knowledge. This not only slows down the system but can also lead to hardware degradation over time.
3. Increased Electricity Bills
The stealthy operation of malicious mining software means that a computer’s CPU and GPU are working overtime. This heightened activity results in increased power consumption, leading to noticeably higher electricity bills for the unsuspecting victim.
4. Potential Hardware Damage
Continuous, intensive mining can push computer hardware to its limits. Overheating can become a real concern, especially if the mining software disables any built-in thermal protections. Over time, this can lead to hardware failures, reducing the lifespan of the device.
5. Unauthorized Data Access and Theft
Beyond just mining, some malicious software seeks to gather more than just computational power. They can snoop on the user’s activities, capture sensitive data, and even access personal files. This breach of privacy can lead to identity theft, financial fraud, and other personal crises.
6. Exposure to Additional Malware
Often, the installation of one piece of malicious software serves as a gateway for more. Once the defenses of a system are compromised, it becomes easier for other malware types, from ransomware to spyware, to find their way in, further endangering the user’s digital security.
7. System Instability
Malicious mining software, especially if poorly coded, can lead to system instability. Users might experience frequent crashes, unresponsive applications, and even the dreaded ‘blue screen of death’ on some systems.
Differentiating Genuine Mining Software from Malware
The surge in cryptocurrency’s popularity has led to a parallel rise in both genuine mining software and their malicious counterparts. For the uninitiated, distinguishing between the two can be akin to navigating a minefield. However, with the right knowledge and tools, users can confidently differentiate genuine mining software from malware and ensure a safe mining experience. Let’s explore the key strategies to make this distinction clear.
1. Source Verification
Official Websites
Always start by downloading mining software directly from the official website of the developer or organization. These sites typically have security measures in place to ensure that the software provided is genuine and free from any malicious add-ons.
Trustable Mining Software Website
WoolyPooly is a recognized mining pool that provides a list of trustworthy mining software. Their recommendations are based on extensive testing and community feedback, ensuring that miners have access to reliable and efficient tools.
Third-party Platforms
If you’re sourcing software from third-party platforms, ensure they’re reputable. Platforms like GitHub, for instance, allow developers to share their code, making it easier for the community to spot any malicious intent.
2. Community Feedback and Reviews
Forums and Discussion Boards
Cryptocurrency communities, like those on Reddit or Bitcointalk, can be invaluable. Users often share their experiences with different software, and any malicious software is quickly flagged by the community.
Software Reviews
Before downloading, look for reviews from trusted tech websites or publications. They often conduct thorough analyses and can provide insights into the software’s legitimacy and performance.
3. Digital Signatures
Genuine software developers often sign their applications with a digital signature. This signature verifies that the software has not been altered since its creation. Most modern operating systems will check for these signatures before allowing an application to run and will warn the user if the signature is missing or invalid.
4. Antivirus and Anti-malware Scans
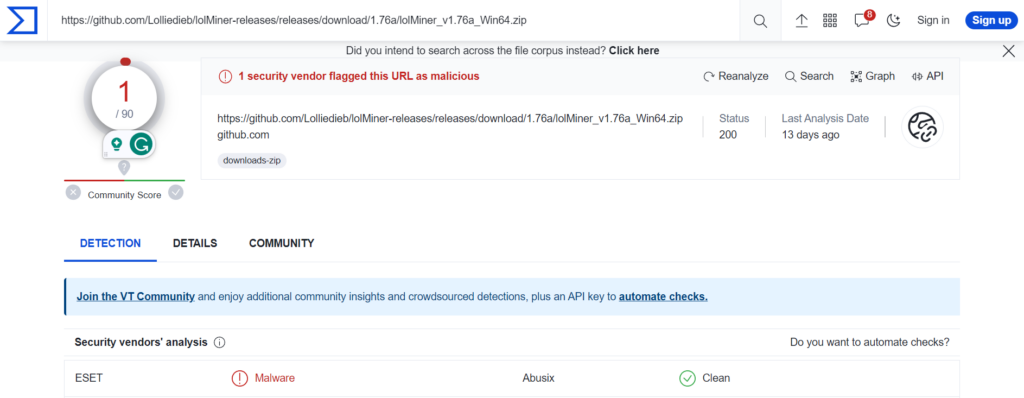
Before you install any mining software, you can justrun it through a reputable antivirus, anti-malware program, or virus total tool. These tools have databases of known malicious signatures and behaviors, allowing them to identify and flag potential threats.
Remember, however, that some genuine mining software might trigger a “false positive” due to their resource-intensive nature. In such cases, cross-referencing with other security tools and community feedback can provide clarity.
5. System Monitoring
After installation, monitor your system’s performance and network activity. Genuine mining software will typically use resources only when you’ve permitted it to run. If you notice unusual activity, like increased CPU usage when the software isn’t running, it could be a red flag.
6. Avoid “Too Good to Be True” Promises
Be wary of software that promises exceptionally high returns or features that seem too good to be true. Malicious actors often bait users with such promises to lure them into downloading malware.
Best Practices for Safe Crypto Mining

Just as miners in the past had to ensure their safety while extracting precious metals, modern crypto miners must take precautions to protect their digital endeavors. Let’s delve into the best practices that every crypto miner should adopt to ensure a secure and efficient mining experience.
1. Use Verified and Trustworthy Mining Software
Source Verification: Always download mining software from reputable sources.
Regular Updates: Ensure that your mining software is always updated. Developers frequently release updates to patch vulnerabilities and enhance performance.
2. Implement Strong Security Protocols
Two-Factor Authentication (2FA): Enable 2FA on all your mining-related accounts, including mining pools and cryptocurrency wallets. This adds an extra layer of security, ensuring that even if your password is compromised, unauthorized access is prevented.
Use Dedicated Email: Consider using a dedicated email address solely for your mining activities. This minimizes the risk associated with potential email breaches.
3. Secure Your Wallet
Cold Storage: For significant amounts of cryptocurrency, consider using cold storage solutions like hardware wallets. These devices are not connected to the internet, making them immune to online hacking attempts.
Backup Regularly: Ensure that you regularly backup your cryptocurrency wallet. Store backups in multiple secure locations, both digital and physical.
Encrypt Your Wallet: Use strong encryption tools to protect your wallet, ensuring that even if your data is accessed, it remains unreadable without the encryption key.
4. Protect Your Hardware
Adequate Cooling: Mining can be resource-intensive, leading to increased heat generation. Ensure that your mining setup has adequate cooling to prevent hardware damage.
Dedicated Mining Hardware: If possible, use dedicated hardware for mining. This separation ensures that your primary devices remain unaffected by the intensive demands of mining and are less exposed to potential threats.
5. Stay Informed and Educated
Join Mining Communities: Engage with online forums, discussion boards, and social media groups focused on crypto mining. These platforms can be invaluable for staying updated on the latest threats and best practices.
Educate Yourself: Regularly read articles, blogs, and research papers related to crypto mining security. The crypto landscape evolves rapidly, and staying informed is crucial.
6. Network Security
Use a VPN: A Virtual Private Network (VPN) encrypts your internet connection, ensuring that all data sent and received is secure from potential eavesdroppers.
Firewall: Ensure that your network has a robust firewall setup to prevent unauthorized access.
Secure Your Router: Change default login credentials for your router and regularly update its firmware.
7. Beware of Phishing Attempts
Always double-check URLs before entering any sensitive information. Be wary of unsolicited emails or messages that direct you to external links or ask for personal details.
8. Monitor System Performance
Regularly check your system’s performance. If you notice unusual activity, such as unexpected high CPU usage, it could be an indication of malicious software running in the background.
Case Studies: Real-life Instances of Mining Malware
The allure of cryptocurrency mining has led many to venture into this digital frontier, hoping to reap lucrative rewards. However, the increasing popularity of crypto mining has also attracted malicious actors who exploit unsuspecting miners. Let’s explore some real-life instances where individuals, lured by the promise of profits, inadvertently downloaded malicious mining software and faced dire consequences.
1. The Deceptive DoubleGun Botnet
Background: In 2020, security researchers discovered a botnet named DoubleGun. This botnet targeted Windows servers, exploiting vulnerabilities to gain control.
The Deception: DoubleGun posed as a legitimate mining software. Once installed, it not only used the victim’s resources for mining but also stole their existing cryptocurrency by replacing wallet addresses with its own.
Outcome: Thousands of servers were compromised, leading to significant financial losses for the victims and substantial illicit gains for the attackers.
2. Fake MinerGate Application
Background: MinerGate is a well-known mining software that allows users to mine various cryptocurrencies. Its popularity made it a prime target for impersonation.
The Deception: Cybercriminals created a fake MinerGate application and distributed it through various channels. Unsuspecting users, believing they were using genuine software, downloaded the application.
Outcome: The fake application contained a trojan that stole users’ crypto wallet credentials. Many users reported unauthorized transactions and loss of funds.
3. The Monero XMRig Hoax
Background: XMRig is a popular open-source software used for mining Monero, a privacy-centric cryptocurrency.
The Deception: Taking advantage of its popularity, malicious actors created counterfeit versions of XMRig and promoted them on forums and websites. These versions came bundled with malware that monitored users’ clipboard actions.
Outcome: Whenever users copied a Monero address (typically done for transactions), the malware replaced the copied address with the attacker’s address. This subtle switch led to users inadvertently sending their Monero to the attacker’s wallet.
4. The Crafty Claymore Impersonation
Background: Claymore is a renowned mining software, widely used for Ethereum mining.
The Deception: Cybercriminals developed a fake version of Claymore and distributed it through ads on search engines and cryptocurrency forums.
Outcome: The fake Claymore software contained a backdoor that allowed attackers remote access to the user’s computer. This access was used to steal cryptocurrency directly from users’ wallets and even hijack their mining operations to mine for the attacker’s benefit.
5. The GitHub Repository Ruse
Background: GitHub, a platform for developers to share and collaborate on code, has been used to host various crypto mining software.
The Deception: Malicious actors created fake repositories mimicking popular mining software. These repositories contained tweaked versions of the software with hidden malware.
Outcome: Unsuspecting miners, believing they were downloading updates or new versions of their favorite mining software, ended up with malware-infested applications. These applications siphoned off a portion of the mined cryptocurrency to the attacker’s wallets.
Conclusion
The intricate dance between crypto mining and security is emblematic of the broader challenges the digital age presents. As we’ve explored, the future of crypto mining is rife with both opportunities and potential pitfalls. The increasing instances where crypto mining software is flagged as malware highlight the pressing need for enhanced security measures and a proactive approach to safeguarding digital assets.
This trend underscores a fundamental truth: with great technological advancement comes an equally significant responsibility to protect and secure. As miners and enthusiasts delve deeper into the world of cryptocurrency, understanding why certain crypto mining software is flagged as malware becomes crucial. It serves as a reminder that in the rush to mine digital gold, ensuring the safety of one’s tools and treasures is paramount.
Moreover, the evolving landscape of crypto mining, shaped by technological innovations, regulatory shifts, and environmental considerations, demands constant vigilance. The instances of genuine mining software being mistakenly flagged are not just technical glitches but indicative of the broader challenges in distinguishing genuine tools from malicious ones in an ever-expanding digital realm.
In essence, as the crypto industry continues its meteoric rise, the intertwined relationship between mining and security will be its linchpin. Ensuring that mining software is genuine, secure, and efficient will not only protect individual miners but also fortify the very foundations of the cryptocurrency ecosystem. The journey ahead, while promising, requires a keen eye, a steady hand, and an unwavering commitment to security.
FAQs
Why is crypto mining software flagged as malware?
Due to unauthorized resource use, cryptojacking, bundling with other malware, and false positives from antivirus software.
How can I ensure my mining software is genuine?
Download from reputable sources, check community feedback, and keep your security tools updated.