In the vast universe of blockchain technology, the term “51% Attack” stands out as a looming specter. But what exactly is it? And why should anyone invested in the crypto world be concerned? This article sheds light on this enigmatic phenomenon, revealing its intricacies and implications for the future of digital currencies.
Table of Contents
What is a 51% Attack?
A 51% attack refers to a potential vulnerability in blockchain networks, particularly those that use a Proof of Work (PoW) consensus mechanism. In such an attack, a single entity or group gains control of more than 50% of a blockchain network’s total computational power, also known as its hashrate.
With this majority control, the attacker can:
- Alter Transaction History: They can rewrite parts of the blockchain, allowing them to erase or change the details of past transactions.
- Double-Spend Coins: The attacker can spend the same coins more than once. For instance, they could send a transaction to a recipient and then, using their majority control, create an alternate version of the blockchain where that transaction never occurred, effectively reclaiming the coins they spent.
- Prevent New Transactions: They can halt the confirmation of new transactions by not including them in the blocks they mine.
The name “51% attack” stems from the fact that the attacker needs just over half of the network’s computational power to carry out these actions. This type of attack undermines the decentralized nature of blockchain, as it allows a single entity to have undue influence and control over the network.
How Does a 51% Attack Work?
Here’s a detailed breakdown of how a 51 percent attack works:
1. Understanding the Basics of Blockchain:
- Decentralization: Blockchains are decentralized networks where multiple participants (nodes) maintain and validate a shared ledger of transactions.
- Consensus Mechanism: For a transaction to be added to the blockchain, the network needs to reach a consensus. In PoW blockchains, this is achieved when miners solve complex mathematical problems to validate transactions and add new blocks.
2. Role of Miners:
- Miners compete to solve these problems, and the first one to solve it gets to add the next block to the blockchain.
- For their efforts, miners are rewarded with the blockchain’s native cryptocurrency.
- The security of PoW blockchains relies on the premise that no single miner or mining pool controls the majority of the network’s total computational power.
3. Gaining Majority Control:
- A 51% attack occurs when a miner or mining pool gains control of more than 50% of a blockchain network’s total computational power.
- With this majority control, the attacker can outpace the rest of the network in block creation.
4. Double Spending:
- The primary threat of a 51% attack is the ability to double-spend coins.
- The attacker can send a transaction to a recipient while also secretly mining a parallel chain where the same coins are sent to another address controlled by the attacker.
- With the majority of the hashing power, the attacker can ensure that their secret chain grows faster than the main chain.
- Once the secret chain is longer than the main chain, it can be broadcasted to the network, which will recognize it as the legitimate chain due to its length.
- This will invalidate the original transaction, allowing the attacker to spend the same coins twice.
5. Rewriting Transaction History:
- With majority control, the attacker can also exclude or modify the ordering of transactions, potentially leading to a loss of trust in the blockchain.
Historical Instances of 51 Percent Attacks
The crypto realm has witnessed several 51% attacks. Some notable instances include:
Ethereum Classic Suffers Second 51% Attack in a Week
Details
Ethereum Classic experienced its third 51% attack within a month, with over 14,000 (in total) blocks being reorganized. This was reported by mining pool Ethermine’s parent entity, Bitfly, and the crypto exchange Binance. As a result, all Ethereum Classic payouts, withdrawals, and deposits were suspended.
While Ethereum Classic developers initially denied any reorganization or 51% attack, blockchain analytics firm Bitquery reported that an attacker double-spent over 800,000 ETC (worth about $5.6 million) and paid around 17.5 BTC ($204,000) to acquire the hash power for the attack.
Implications
The reorganized transaction history became the longest chain on the network. However, the majority of Ethereum Classic miners, including Ethermine, continued to mine on the shorter version of the network. Due to the recent network attacks, exchanges and mining pools were advised to significantly increase confirmation times for all deposits and incoming transactions.
Cause
A chain reorg happens when an entity gains more hashing power than the rest of the network’s miners. This allows the entity to rewrite the chain’s history and double-spend the blockchain’s native currency. In this case, the hashing power on Ethereum Classic had decreased considerably.
Bitcoin SV: A Target of Multiple 51% Attacks
Bitcoin Satoshi’s Vision (BSV), a fork of the Bitcoin (BTC) blockchain, has been a notable target for 51% attacks. Over a span of a few months, BSV experienced multiple blockchain reorganization (reorg) attacks, which are indicative of 51% attacks.
Three Attacks in Three Months
Between June 24 and July 9, Bitcoin SV suffered from four separate attempted 51% attacks. These attacks resulted in double-spent coins being sent to the Bitmart crypto exchange. The June 24 and July 1 attacks reportedly went unnoticed initially, with investigations commencing only after the July 6 incident. Some exchanges, like Huobi, temporarily paused deposit and withdrawal services for BSV in response.
In August, Bitcoin SV faced another suspected 51% attack. This was similar to the previous incidents that occurred between the end of June and the first week of July. During this attack, the malicious actor compromised about 10 hours’ worth of transactions on the Bitcoin SV chain.
Modus Operandi
The attackers, in both sets of incidents, used similar methods. In the June and July attacks, the attacker used the pseudonym “Zulupool” (not connected to the legitimate Hathor Network miner of the same name). In contrast, the August attacker impersonated the Taal mining pool.
The primary threat of these attacks was the ability to double-spend coins. In the June and July attacks, double-spent transactions were detected, but it’s unclear if the August attacker was successful in sending double-spent BSV to any exchange.
Response and Mitigation
In response to the attacks, the Bitcoin Association advised honest node operators to mark the false chains initiated by the hacker as invalid. This is crucial to prevent the attackers from gaining any economic benefit, such as double-spending.
These incidents underscore the vulnerabilities that some blockchains face, especially when there’s a significant drop in hashing power. It’s crucial for networks to maintain a high level of security to prevent such attacks.
Implications of a 51% Attack

A 51% attack, one of the most significant vulnerabilities in blockchain networks, can have profound implications. Here’s a detailed exploration of its consequences:
1. Integrity of the Blockchain:
- Immutability Compromised: One of the core principles of blockchain is its immutability, meaning once data is added, it cannot be altered. A 51% attack can rewrite parts of the blockchain, undermining this principle.
- Loss of Trust: If users and investors believe that a blockchain can be easily altered, they may lose trust in that blockchain’s reliability and security.
2. Financial Implications:
- Double Spending: The primary threat of a 51% attack is the ability to double-spend coins. This means an attacker can spend the same coins more than once, leading to potential financial fraud.
- Monetary Losses: Successful double-spending can result in significant financial losses for users, exchanges, and other entities that accept the cryptocurrency.
- Market Value Impact: News of a 51% attack can lead to a sharp decline in the cryptocurrency’s market value as investors and users lose confidence.
3. Operational Disruptions:
- Transaction Reversals: An attacker with majority control can reverse transactions that they sent while they were in control, leading to disruptions in the normal flow of operations on the blockchain.
- Transaction Halts: The attacker can potentially halt the confirmation of new transactions, causing a standstill in the network’s operations.
4. Security Concerns:
- Increased Vulnerability: Once a network has been successfully attacked, it may be perceived as more vulnerable, attracting more malicious actors to exploit it further.
- Chain Splits: In some cases, to counteract a 51% attack, the community might opt for a hard fork, leading to a split in the blockchain. This can result in the creation of two separate chains, each with its own version of the transaction history.
5. Reputational Damage:
- Loss of Credibility: A successful 51% attack can tarnish the reputation of the affected blockchain. This can deter new users and investors from joining the ecosystem.
- Impact on Partnerships: Businesses and other entities partnered with the affected blockchain might reconsider their association due to the security concerns.
6. Ecosystem Impact:
- Exchanges: Cryptocurrency exchanges might delist the affected coin or increase the number of confirmations required for transactions, making it more cumbersome for users.
- Miners: Miners might abandon the affected blockchain in search of more secure and profitable alternatives, leading to a further decrease in the network’s hashing power and increasing its vulnerability.
7. Broader Implications:
- Influence on Regulation: Repeated 51% attacks can draw regulatory scrutiny, with authorities potentially introducing stricter regulations for blockchain operations.
- Perception of Blockchain Technology: Such attacks can also influence the broader perception of blockchain technology, making people skeptical about its touted security benefits.
In essence, while a 51% attack is a technical vulnerability, its implications span across financial, operational, reputational, and even regulatory domains. It underscores the importance of robust security measures and a vigilant community in the world of decentralized systems.
Measures to Prevent a 51% Attack

1. Increasing Hashrate:
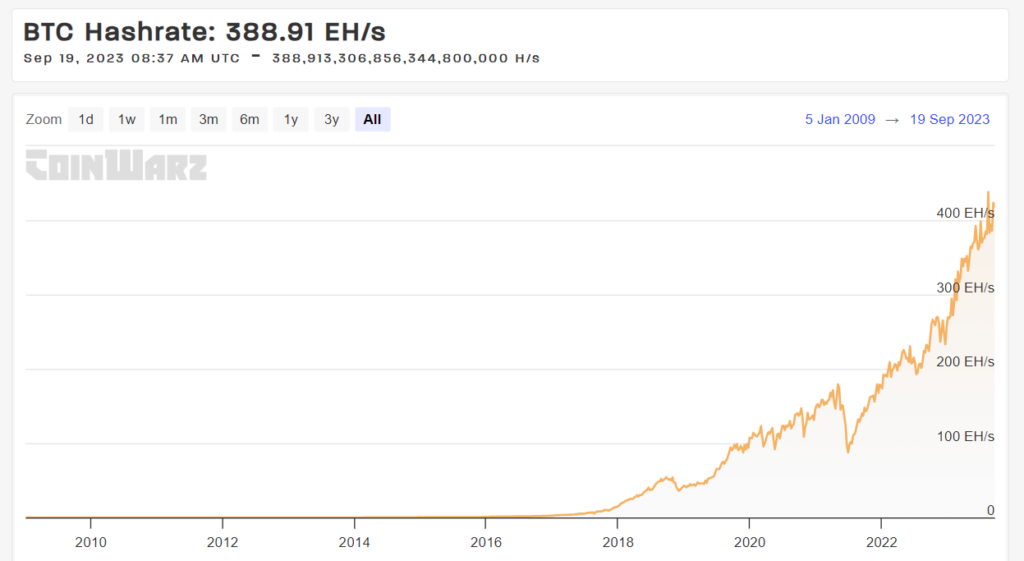
- Strengthening Security: A blockchain with a high combined computational power (hashrate) is harder to attack. The more decentralized the mining power, the more secure the network becomes, as it’s more challenging for a single entity to gain majority control.
- Encouraging More Miners: By offering better mining rewards or optimizing the mining process, a blockchain can attract more miners, thereby increasing its total hashrate.
2. Building a Wealth Network:
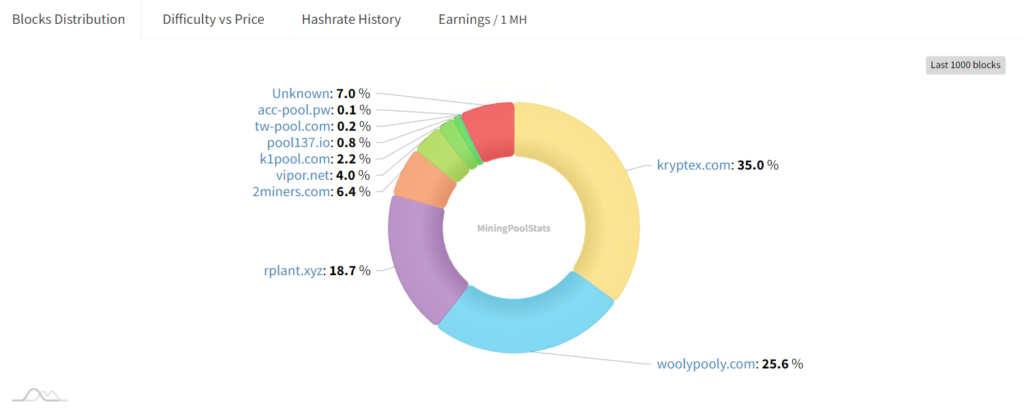
A wealth network refers to a decentralized ecosystem of mining pools where participants contribute their computational resources to validate and secure a blockchain. The primary objective of a wealth network is to ensure that the control and influence over the blockchain are widely distributed, reducing the risk of any single entity gaining majority control.
3. Adopting Alternative Consensus Mechanisms:
- Proof of Stake (PoS): Unlike PoW, which relies on computational power, PoS requires validators to hold and “stake” cryptocurrency as collateral to validate transactions. This makes 51% attacks financially prohibitive because an attacker would need to own a majority of the cryptocurrency, which is costly and would devalue with a successful attack.
- Delegated Proof of Stake (DPoS): In DPoS, a limited number of trusted validators are elected by the community to create blocks. This reduces the risk of a 51% attack but centralizes the process to some extent.
4. Penalizing Malicious Actors:
- Cryptographic Techniques: Some blockchain designs include cryptographic methods that can detect and penalize malicious activities, making it expensive and risky for attackers.
- Loss of Staked Coins: In PoS systems, malicious actors can lose their staked coins if they’re caught trying to attack the network.
5. Time-Locked Transactions:
- Delaying Transaction Finality: By introducing a time-lock for transactions, it becomes harder for an attacker to double-spend as they would need to maintain control of the majority hash power for a more extended period.
6. Multi-Blockchain Solutions:
- Merged Mining: This allows a miner to mine on multiple blockchains simultaneously. It can increase security as attacking one blockchain would require attacking the others as well.
- Interchain Linking: Linking smaller, less secure blockchains to more secure ones can enhance the security of the former.
7. Increased Confirmations for Transactions:
- Raising Confirmation Requirements: Exchanges and wallets can increase the number of required confirmations for a transaction to be considered final. This makes it harder for an attacker to execute a double-spend, as they would need to maintain control for a longer time.
8. Active Network Monitoring:
- Vigilant Community: A proactive and vigilant community can detect unusual mining activities or transaction patterns, raising alarms before an attack can cause significant damage.
- Real-time Analytics: Implementing real-time analytics tools can help in early detection of potential 51% attacks.
9. Educating the Community:
- Awareness: Educating users, miners, and stakeholders about the risks and signs of a 51% attack can foster a more vigilant community.
- Best Practices: Encouraging best practices among exchanges, such as waiting for more confirmations during times of suspected increased risk, can mitigate potential damages.
In essence, while no single solution can guarantee complete protection against 51% attacks, a combination of technical measures, community vigilance, and continuous research can significantly reduce the risk.
Future of Blockchain Security
As blockchain continues to evolve, so do the threats against it, necessitating the development of advanced security measures. Here’s a detailed exploration of the future prospects and challenges in blockchain security:
1. Quantum Computing Threat:
- Quantum Challenge: Quantum computers, once they become sufficiently powerful, pose a potential threat to current cryptographic methods used in blockchains. Quantum algorithms could potentially break widely-used cryptographic schemes like RSA and ECC much faster than classical computers.
- Post-Quantum Cryptography: Research is ongoing to develop cryptographic methods that are resistant to quantum attacks. These new algorithms aim to secure blockchains even in a world where quantum computers are prevalent.
2. Layered Security Protocols:
- Multiple Layers: Instead of relying on a single security protocol, future blockchains might implement multiple layers of security measures to ensure that even if one layer is compromised, the overall system remains secure.
- Adaptive Systems: Blockchains could be designed to adapt and change their security protocols in real-time based on detected threats.
3. Decentralized Identity Verification:
- Self-Sovereign Identity: This concept allows individuals to own, control, and share their personal information without centralized authorities. It can enhance security by reducing the risks associated with centralized data breaches.
- Biometric Verification: Integrating biometric data like fingerprints or retina scans can provide an additional layer of security for user verification on blockchains.
4. Advanced Consensus Mechanisms:
- Beyond PoW and PoS: As the limitations of Proof of Work (PoW) and Proof of Stake (PoS) become evident, research is ongoing to develop new consensus mechanisms that are more energy-efficient, scalable, and secure.
5. Interoperability and Security:
- Cross-Chain Operations: As multiple blockchains aim to communicate and operate with each other, ensuring the security of cross-chain operations will be crucial.
- Standardized Security Protocols: There might be a push towards standardizing security measures across different blockchains to ensure consistent security levels.
6. AI and Machine Learning Integration:
- Real-time Threat Analysis: AI algorithms can analyze vast amounts of data in real-time to detect and counteract suspicious activities on the blockchain.
- Predictive Security: Machine learning models can predict potential security threats based on historical data, allowing for proactive measures.
7. Enhanced Privacy Protocols:
- Zero-Knowledge Proofs: Techniques like zk-SNARKs allow for transaction validation without revealing the transaction’s details, enhancing privacy and security.
- Homomorphic Encryption: This allows computations on encrypted data without decrypting it, ensuring data privacy while still enabling its use in applications.
8. Regulatory and Governance Models:
- Global Collaboration: As blockchain adoption becomes global, there might be collaborative efforts between countries to establish standardized security and regulatory protocols.
- Decentralized Governance: Blockchain networks might adopt decentralized governance models, allowing the community to propose, vote on, and implement security upgrades.
9. Education and Awareness:
- Training Programs: As blockchain becomes mainstream, there will be a greater emphasis on educating developers, users, and stakeholders about best security practices.
- Community Vigilance: A well-informed and vigilant community can act as a first line of defense against potential threats.
In conclusion, the future of blockchain security is a dynamic landscape, with challenges and innovations going hand in hand. As the technology matures and its adoption widens, ensuring its security will remain a top priority for developers, businesses, and governments alike.
Conclusion
Blockchain’s allure lies in its decentralized promise, a beacon of trust in a digital age. Yet, the specter of the 51% attack serves as a stark reminder of the delicate balance between decentralization and vulnerability. While executing such an attack on prominent blockchains is a formidable challenge, the threat remains palpable for emerging networks, emphasizing the critical role of innovation and adaptability in blockchain security.
The crypto community‘s response to these challenges has been commendable. The crypto realm’s proactive strides, from delving into alternative consensus mechanisms to leveraging the prowess of AI for enhanced security, showcase the industry’s resilience and forward-thinking approach. As quantum computing looms on the horizon, the race to fortify cryptographic defenses intensifies, underscoring the dynamic interplay between technological advancement and security imperatives.
For every participant in the blockchain ecosystem, awareness of these challenges and the evolving solutions is essential. As we navigate the future of blockchain, the journey is not just about harnessing its transformative potential but also about preserving its integrity and trustworthiness. In this dance of power, innovation, and security, the enduring success of blockchain will hinge on our collective commitment to safeguarding its foundational principles.
FAQs
What triggers a 51% Attack?
A single entity gaining control of over half the network’s computational power.
Has any major cryptocurrency faced a 51% Attack?
Yes, Ethereum Classic and Bitcoin Gold are notable examples.
How difficult is to execute a 51% attack? Why?
Executing a 51% attack is challenging because it requires an attacker to gain control of more than half of a blockchain network’s total computational power. This is especially difficult on large, well-established blockchains with high hashrates, as amassing such power would require significant financial and technical resources.
How to stop a 51% attack?
Stopping a 51% attack involves increasing the network’s decentralization, and actively monitoring for unusual mining activity. Additionally, exchanges can increase the number of confirmations required for transactions, making it harder for an attacker to double-spend successfully.


